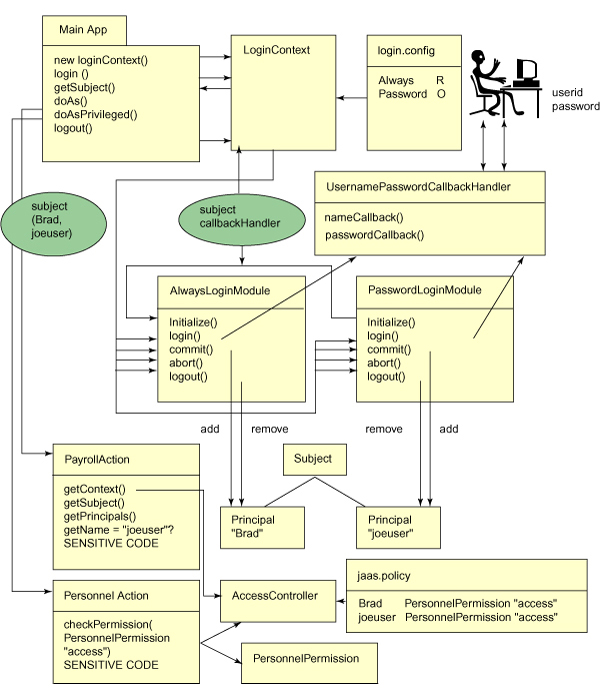
In this tutorial, we will look at code for a JAAS example application, piece by piece. To help keep track of the big picture, the figure below shows how all of these pieces fit together. The running example (main program JAASExample) first authenticates a user using two techniques, or login modules, and then allows or disallows (or authorizes) access to two pieces of sensitive code based on the results of the authentication step.
Here is a diagram of the JAASExample program. The flow of operations is described in the next panel.