Leased line VPNs are usually dial-up in nature and are
used by companies that already have the needed multiple
points-of-presence available.
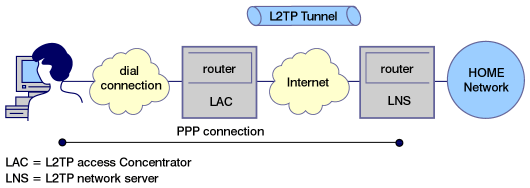
Layer 2 Tunnel Protocol (L2TP) was created by the IETF
to extend a
PPP connection past the connecting ISP's POP, all the way to the
corporate gateway. Because PPP can run different transport protocols
than IP, the remote host can appear to be on the same subnet as
the corporate gateway with PPP tunneling the gateway protocol under
the IP protocol. Figure 2 shows one L2TP scenario, with
the disparate elements of the actual network connection shown.
Figure 2